How to extract a PDF from an app.
To prevent piracy some apps go above and beyond to safeguard their PDF-s. But not far enough, so let me take you on a journey on how I got a PDF of the notes I wanted!
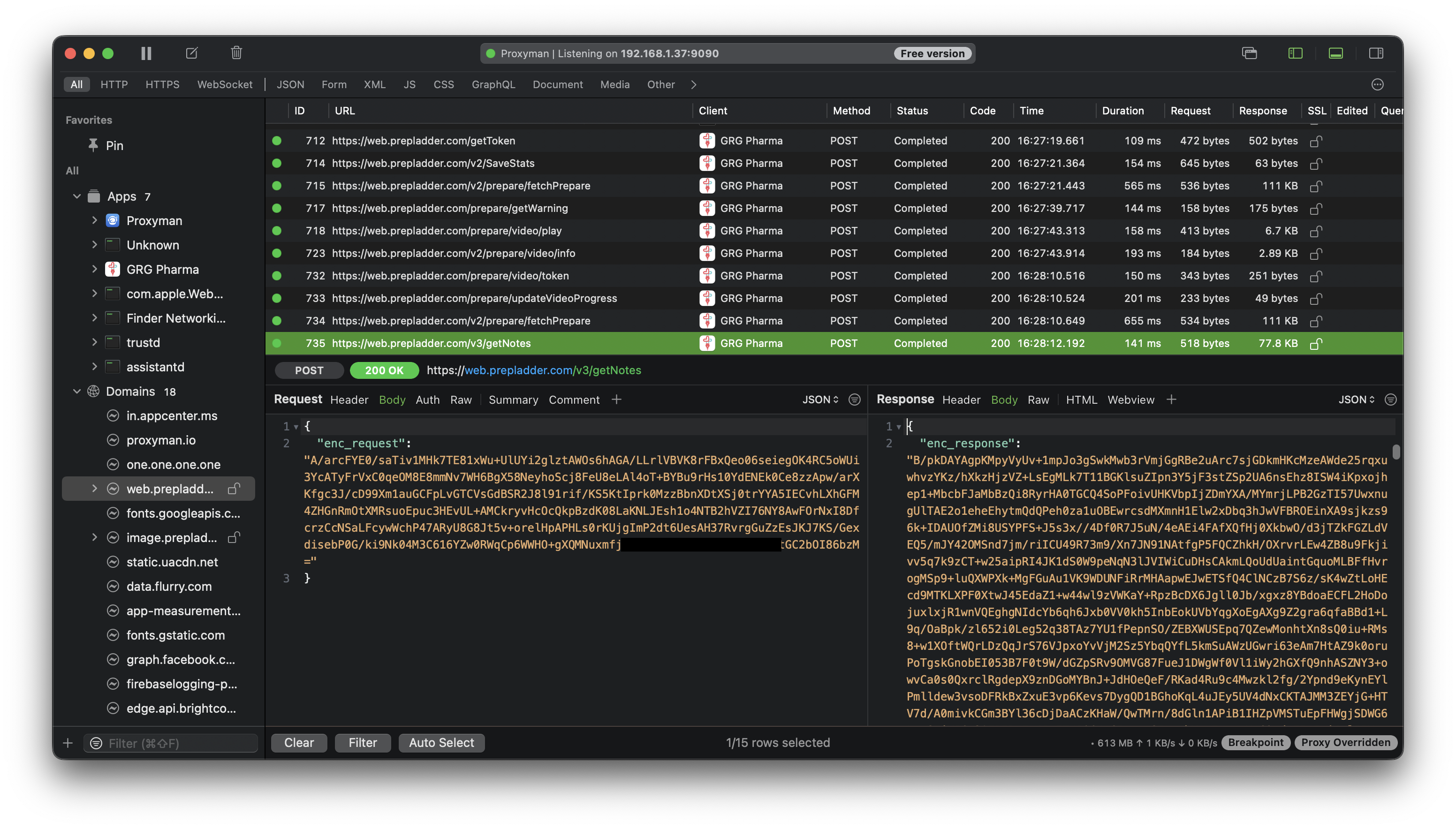
I used Proxyman to capture the http requests and responses while opening the notes in the app
The requests and responses both were encrypted. This was going to be harder than usual.
But all hope was not lost because they didn't obfuscate their android app! Onwards to decompiling!
A simple APK download and decompilation using jadx later, we have near about the source code ready to be inspected!
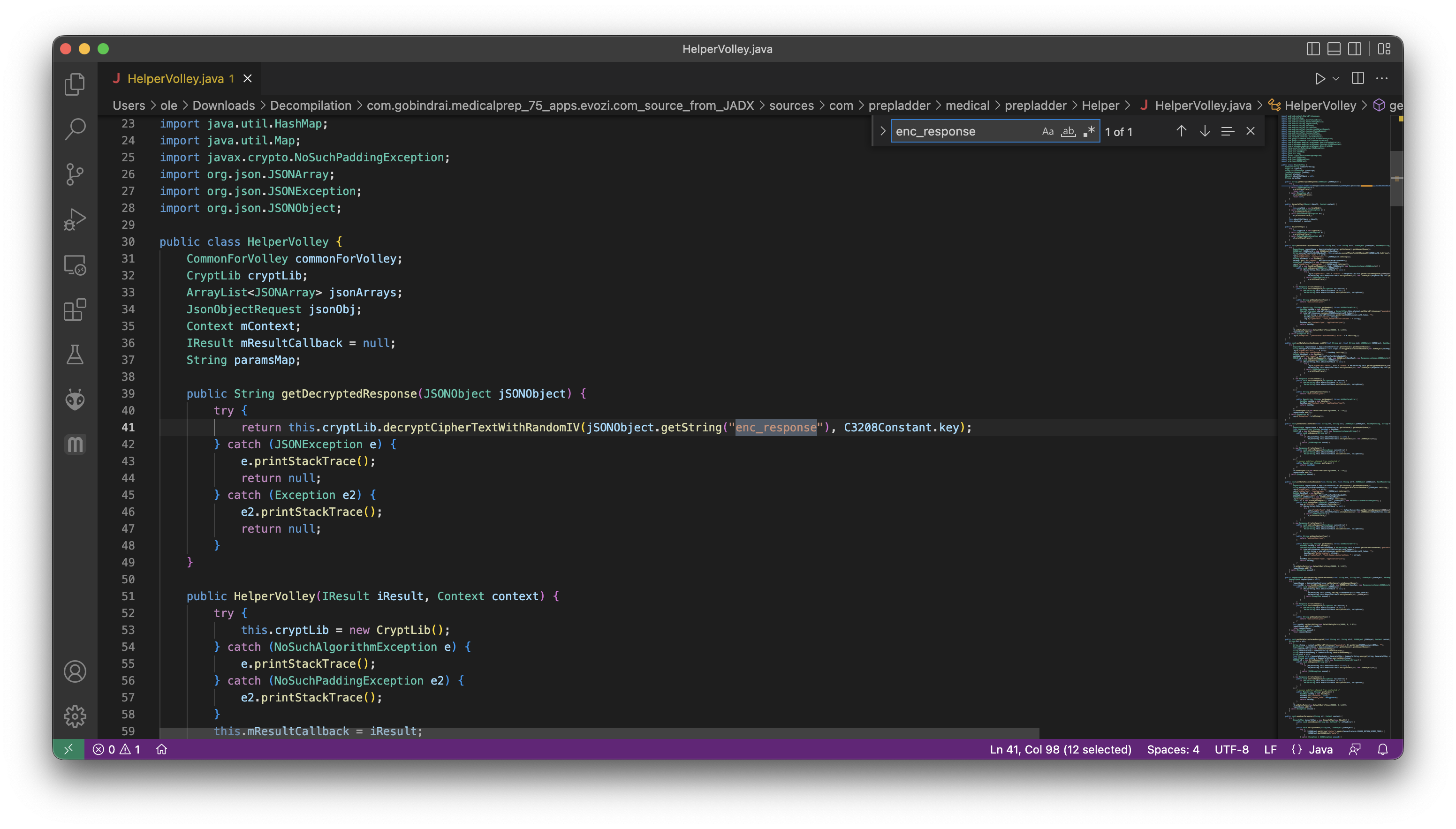
It didn't take long to find the method where 'enc_response' was being handled.
And here was the method call itself.
Now to find the method 'decryptCipherTextWithRandomIV' and parameter 'C3208Constant.key'.
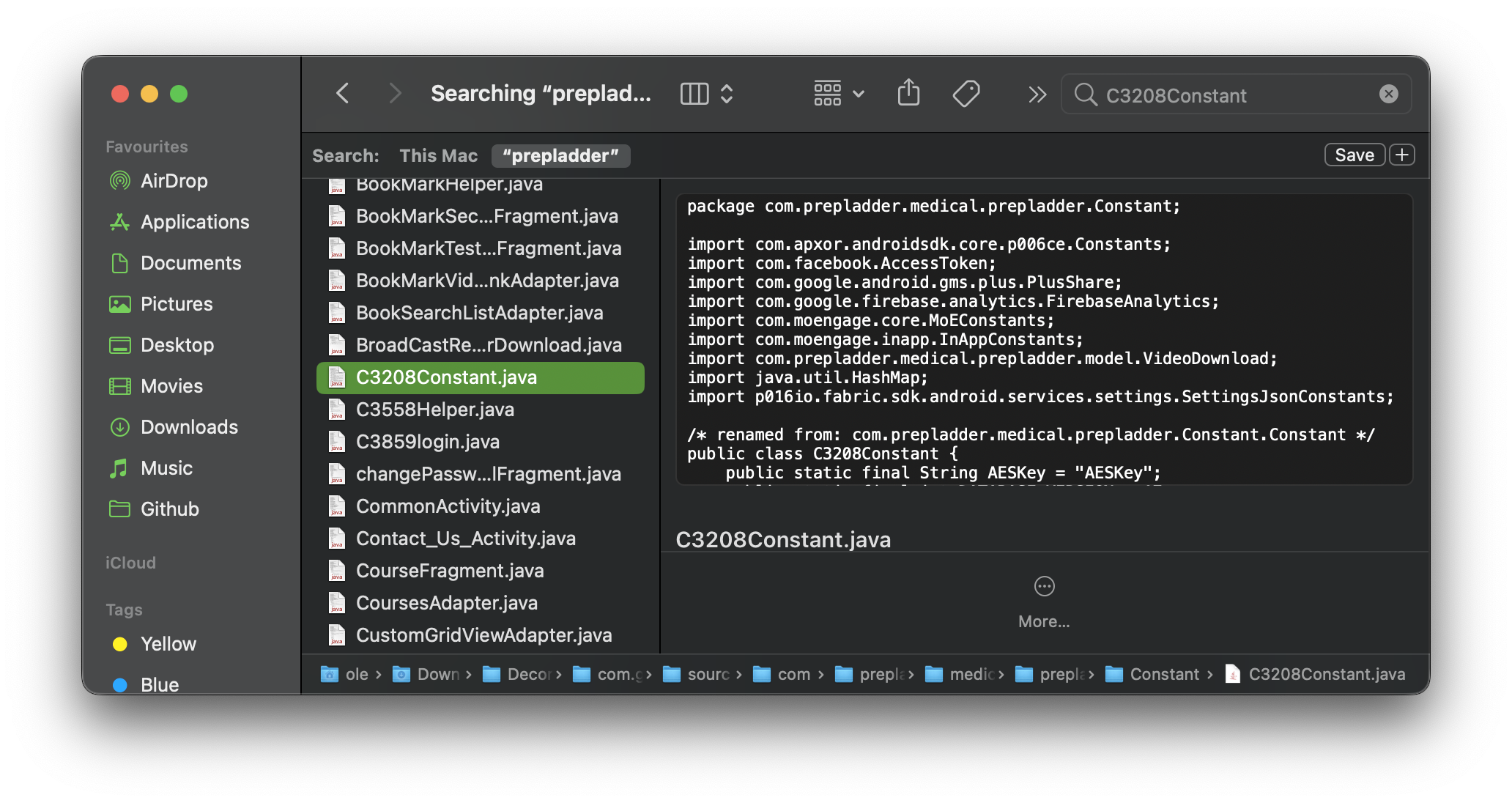
The key was in a class called C3208Constant and it was basic gibberish. The class name was lost in the decompilation process so jadx gave it a more understandable name. And yes, C3208Constant is (much) better than aaaaab.
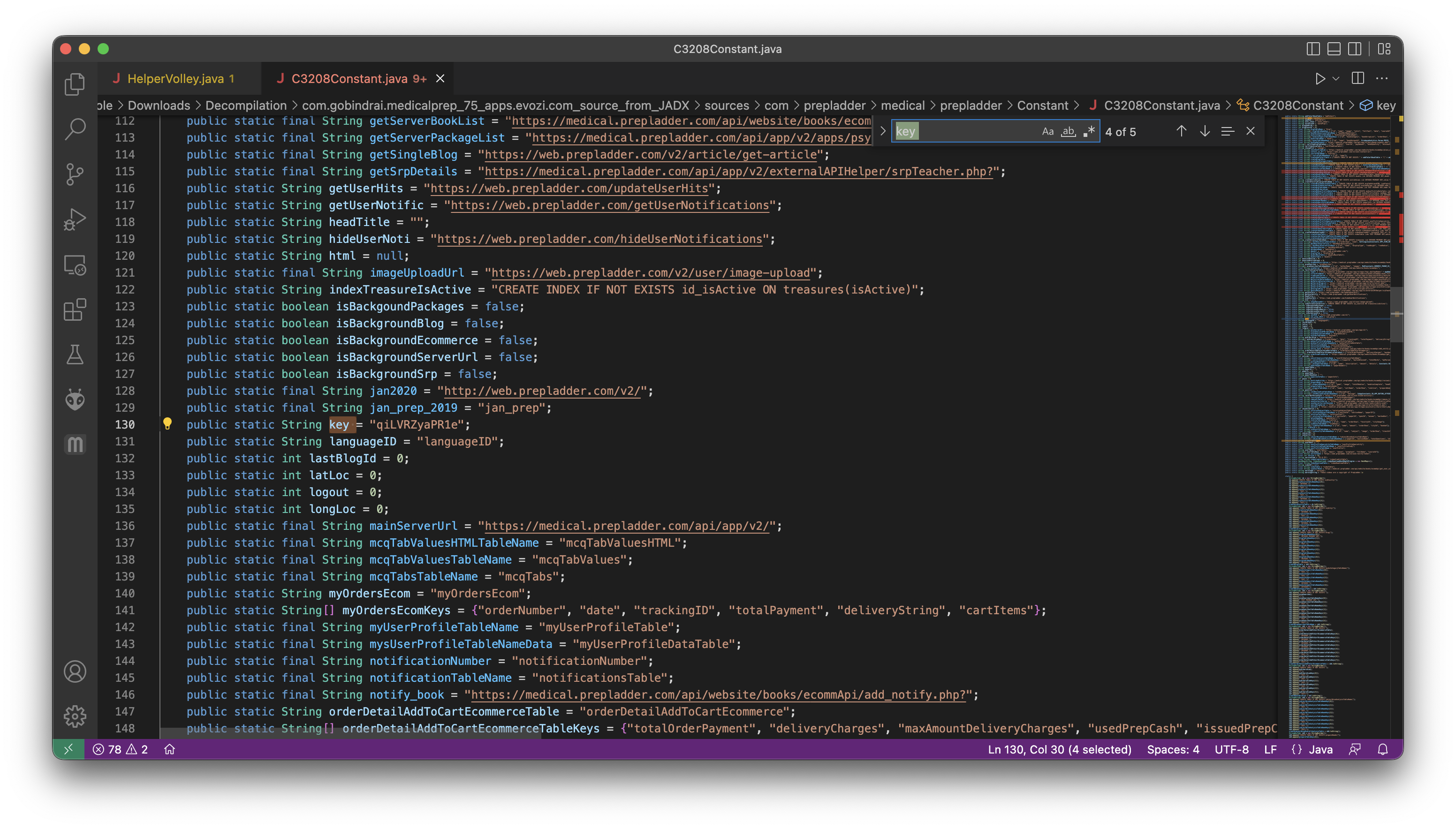
The function itself was also easy to find with a quick Cmd+F.
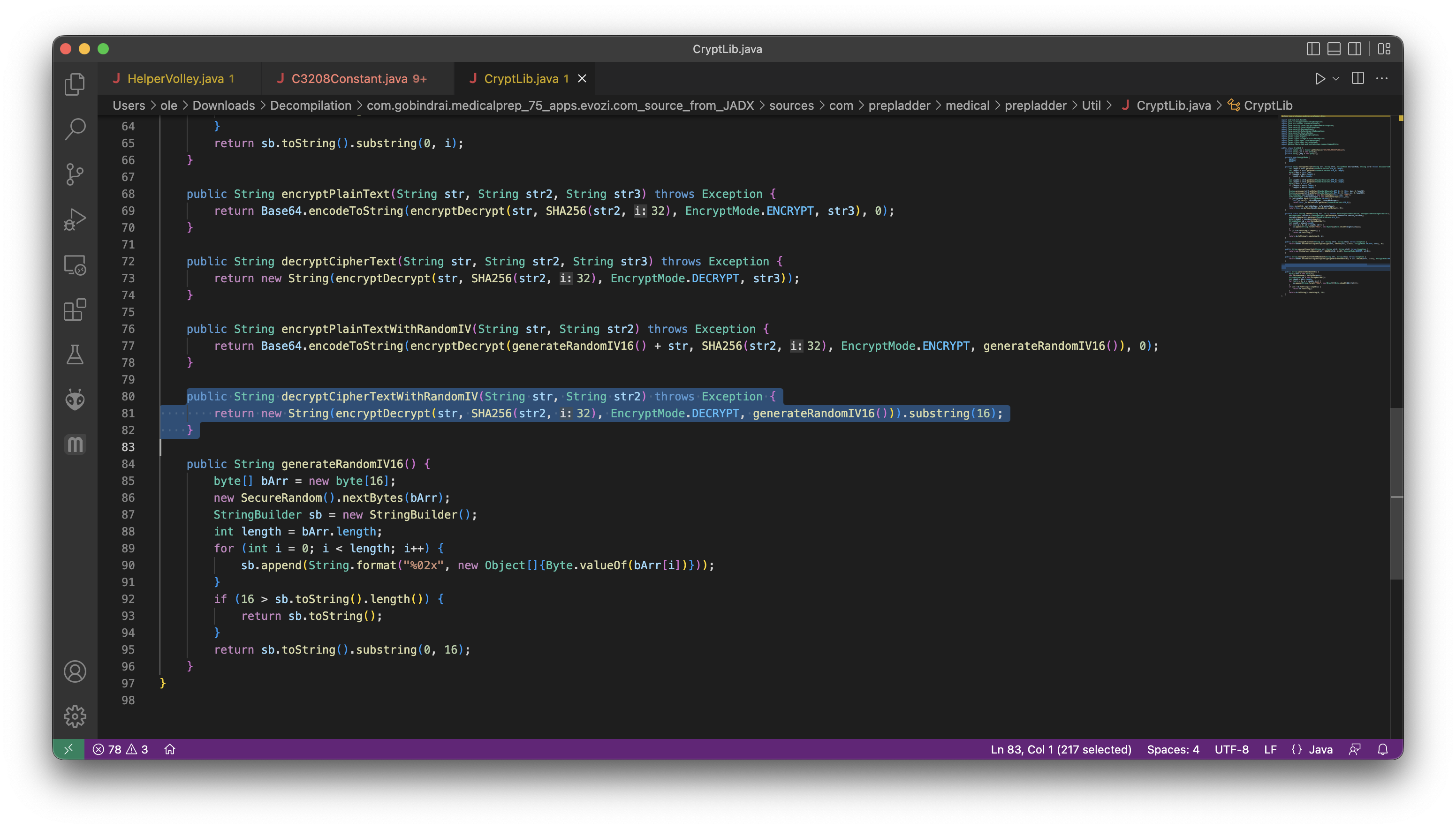
We have everything we need now to run this method to decrypt the http response. Since this is an Android app and in Java I made a dummy Android app instead of a simple Java file. This will save a lot of headache later.
All done, let's see what this function outputs!
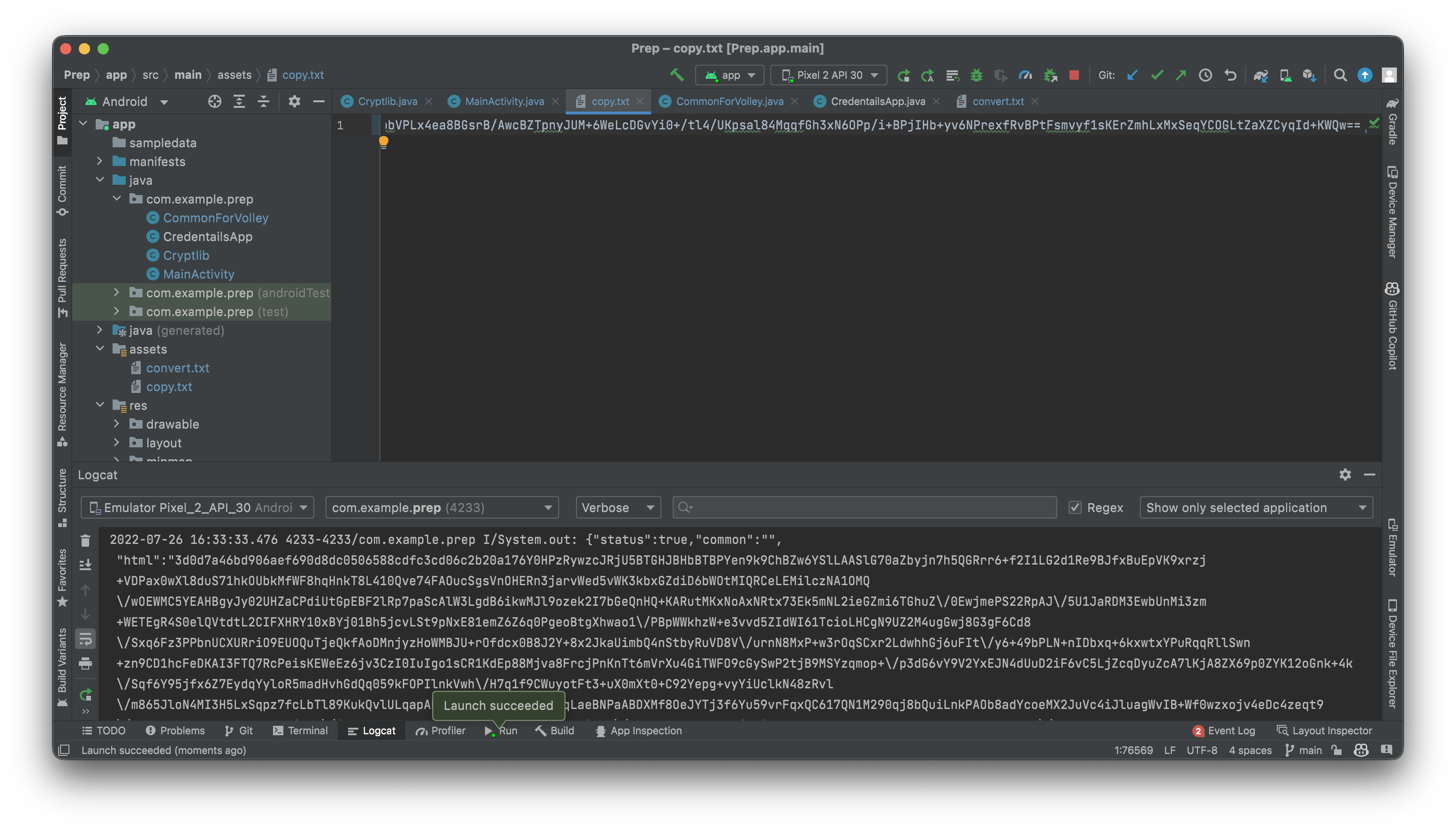
Huh. Look below in the logcat. We have something. The encryption has been cracked! But wait... Another one?! The response has been encrypted TWICE?! The html we seek is hidden behind one(?) more layer of encryption?! Oh well back to Cmd+F to find out how to decrypt this now.
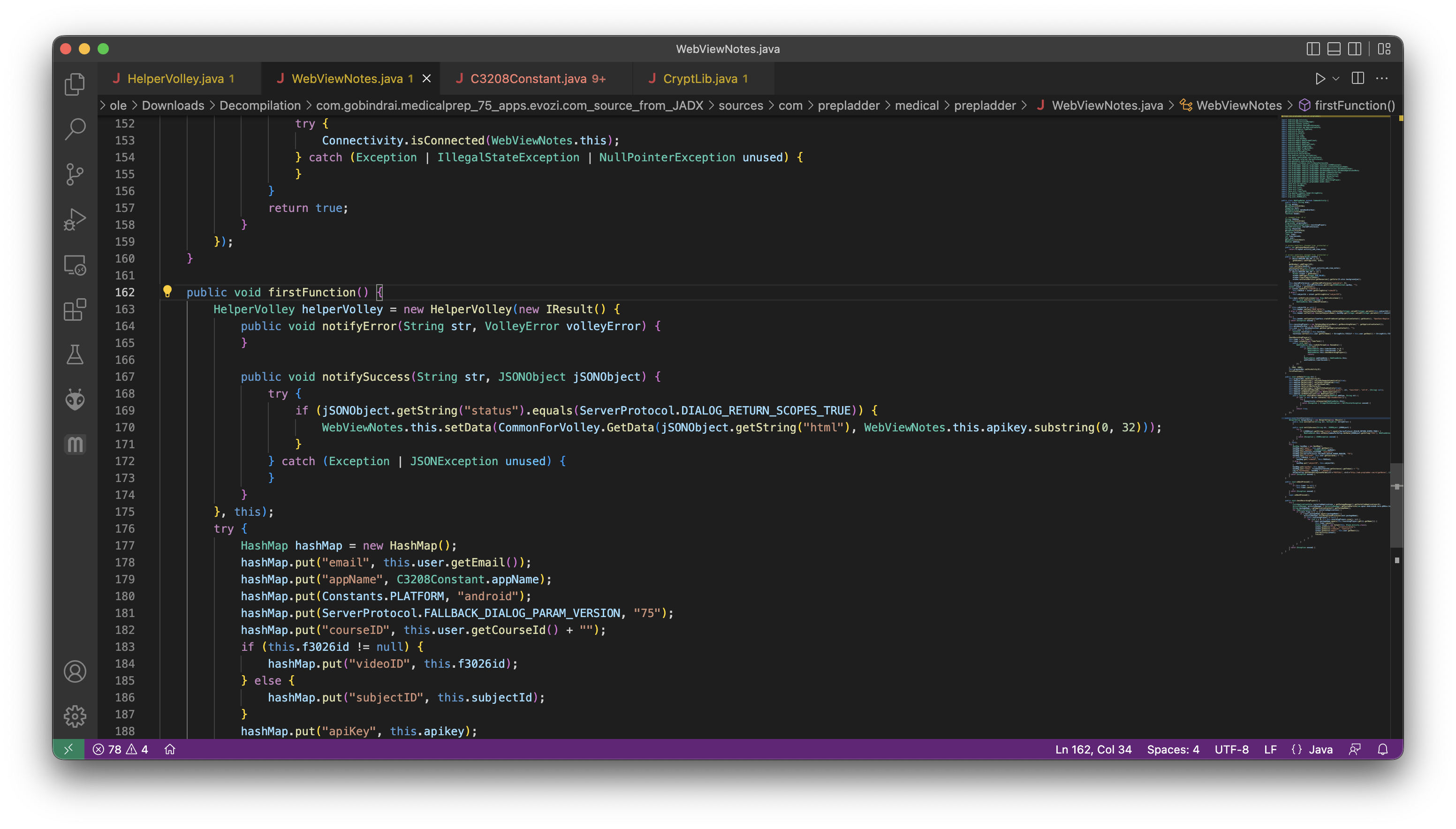
So this is the method responsible for making sense of that gibberish html. This took a while to find because the term 'html' was a common occurance.
But our troubles are still not over. This method needs an apiKey and we have none. A deeper look into the code tells us the apiKey is included in the REQUEST body. Who would've guessed?
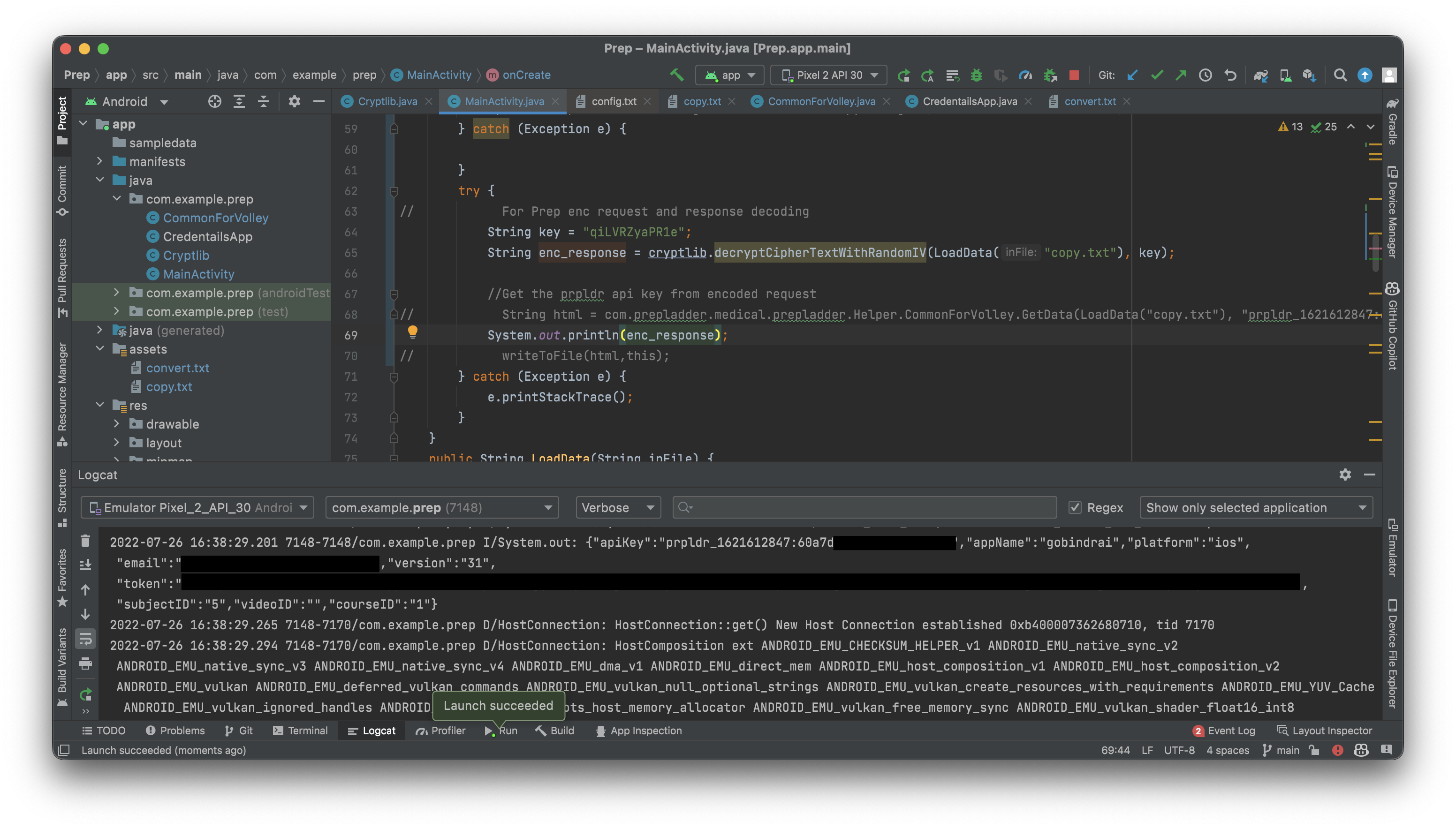
Gotcha! And to implement this method in our dummy Android app like before.
...
One last encryption reversal later using our newfound apiKey later and voila ->
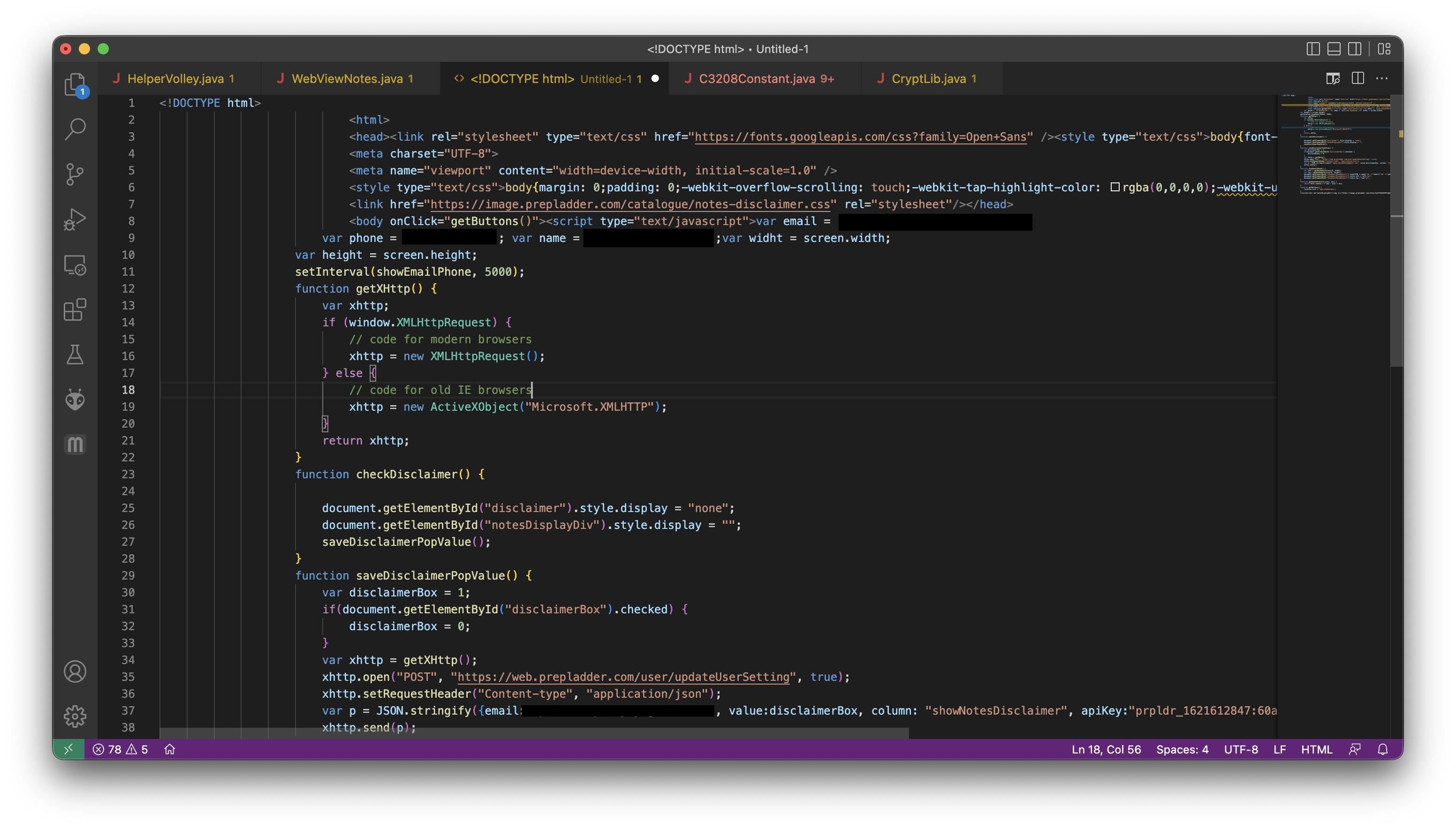
We have the html file! Now let's dig deeper to check if this has what we need...
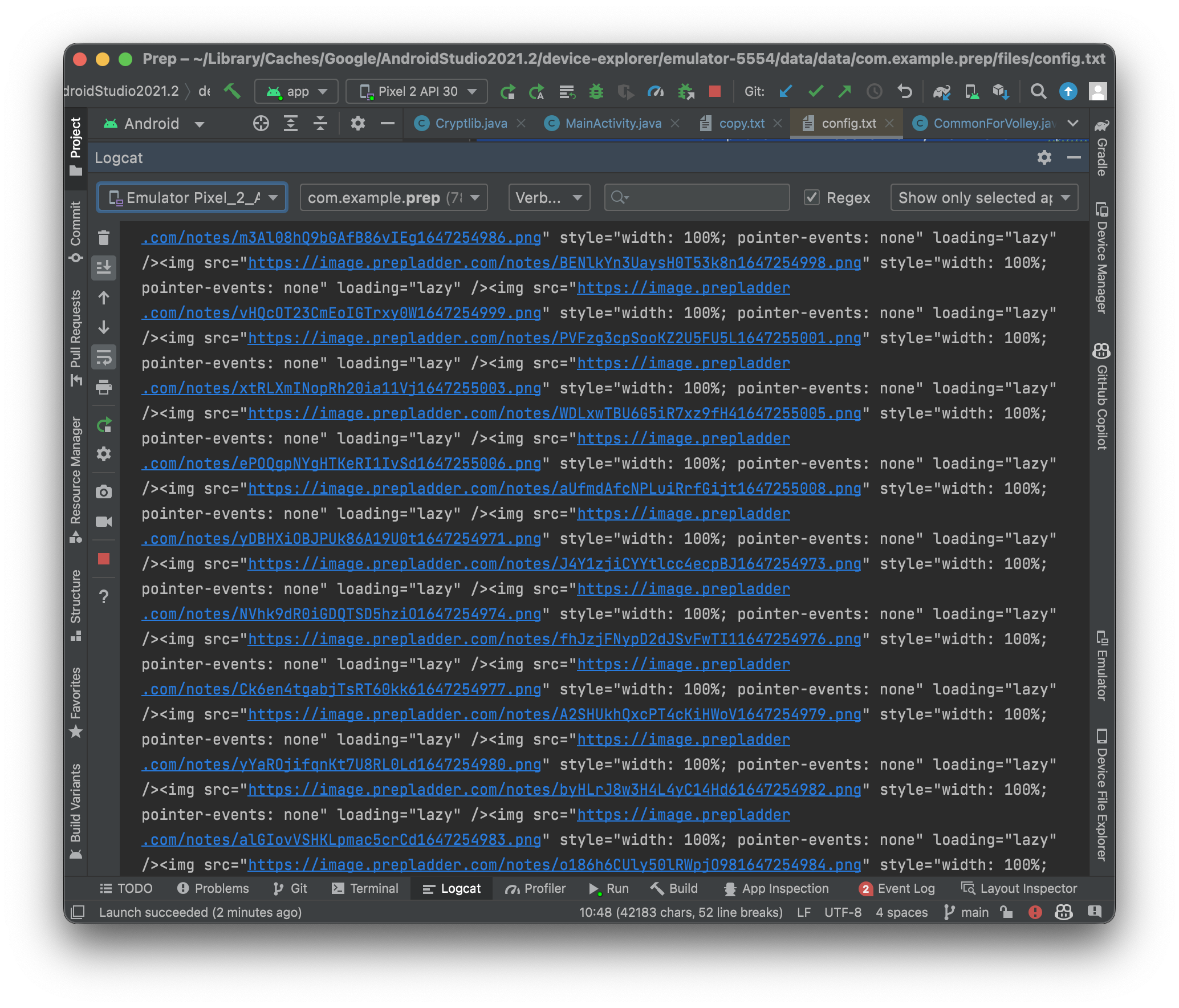
...and there's the notes we wanted! Now simply a matter of opening the file in Chrome and saving it as a PDF!
And we are done! I really should be studying these notes now.
27th July, 2022.